Request Your Free Analyst Report Now:
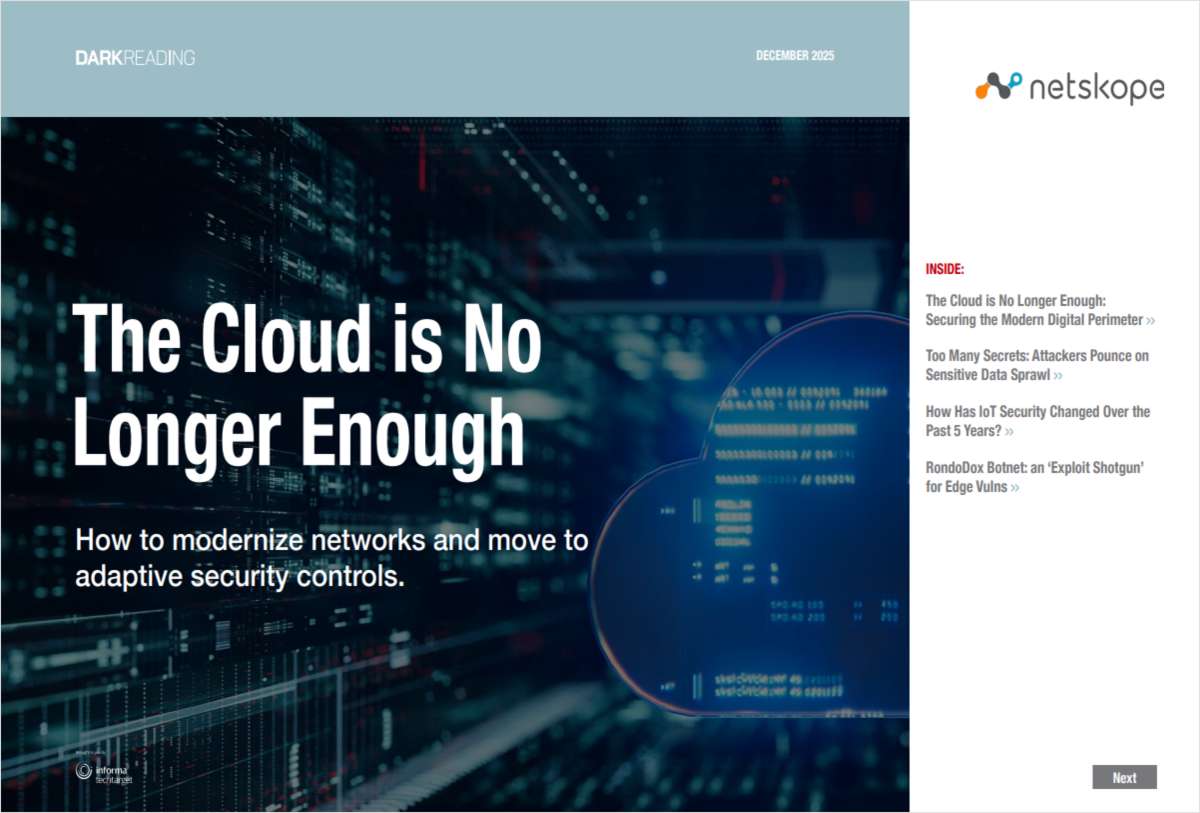
"The Cloud is No Longer Enough"
Driven by cloud, AI, IoT, the remote workforce, and an expanding edge, the dissolution of the perimeter poses unprecedented performance and security challenges. Here’s how to modernize and move to adaptive security controls for today’s networks.
In an era where digital transformation is reshaping industries, cybersecurity professionals face unprecedented challenges in safeguarding sensitive data and maintaining secure networks. This report examines the evolving landscape of cloud security, edge environments, and sensitive data sprawl. It explores how attackers are exploiting vulnerabilities in modern systems, including hardcoded credentials, API keys, and access tokens, which are increasingly ending up in unexpected places. The report emphasizes the critical need for adaptive security controls and innovative governance strategies to address these threats effectively.
The report provides a comprehensive analysis of recent high-profile breaches and their implications for organizations. It highlights how exposed secrets, poor secret hygiene, and over-privileged credentials are creating vulnerabilities that attackers are quick to exploit. With the rise of AI-driven coding platforms and generative tools, the volume of secrets being mishandled is growing, further complicating the security landscape. This report offers actionable insights into mitigating these risks, including strategies for improving secret hygiene, implementing automated compliance measures, and adopting short-term credentials to limit damage from exposed secrets.
Cybersecurity professionals will find this report highly relevant to their roles as it provides practical solutions to modern security challenges. By integrating security into operations and adopting intelligent, adaptive measures, organizations can gain a competitive edge while protecting their digital assets. The report serves as a vital resource for understanding the complexities of distributed environments, supply chain risks, and the importance of proactive governance in securing sensitive data.
After reading this report, you will...
- Understand the risks posed by sensitive data sprawl and how attackers exploit exposed secrets in modern systems.
- Learn strategies to improve secret hygiene, including effective monitoring, scanning, and removal of secrets from unintended channels.
- Gain insights into mitigating supply chain risks and securing developer resources against breaches and unauthorized access.
- Discover how adaptive security controls and automated compliance measures can enhance your organization’s security posture and resilience.
Offered Free by: Netskope
See All Resources from: Netskope